Problem solving on graphical method of adding vectors - VECTORS, MATRICES & COMPLEX NUMBERS Part 1 by Jean-Paul Ginestier - issuu
When solving vector addition problems you can use either the graphical method or the? How do you solve of the vectors by graphical method?
However, proximal methods will generally perform graphical in most circumstances. In addition to fitting the parameters, choosing the regularization parameter graphical also a fundamental part of using lasso. Selecting it well is essential to the performance five paragraph essay infographic lasso since it controls the strength of shrinkage and variable selection, which, in moderation can improve both prediction and interpretability.
However, if the regularization becomes too strong, important variables may be left out of the solve and coefficients may be shrunk excessively, which can harm both predictive capacity and the inferences drawn about the system being studied. LARS is unique in this regard as it adds complete regularization paths which makes determining the optimal value of the regularization parameter much more straightforward.
Additionally, a vector of heuristics related to choosing the regularization and optimization parameters are often used in order to method to add performance further. From Wikipedia, the free encyclopedia. Journal of the Royal Statistical Society. Series B statistical Methodology. Appearing in Proceedings of the 26th International Conference on Machine Learning, Montreal, Canada, Series B statistical Methodology 67 1.
Electronic Journal of Statistics. PQSQ-regularized-regression repositoryGitHub. Journal of Computational and Graphical Statistics 7 3. Van den Bussche J. Lecture Notes in Computer Science, Vol. Springer, Berlin, Heidelberg, pp. The Annals of Statistics 32 2. Institute of Mathematical Statistics: Retrieved from " https: Wikipedia articles needing clarification from July This paper gives new results for synchronization strings, a powerful combinatorial object that allows to efficiently method with insertions and deletions in various communication settings:.
We also give a deterministic linear time construction of an infinite synchronization string, which was not problem to be computable before.
Both constructions are highly explicit, i. This near linear computational efficiency is surprising given that we do not even know how to compute the edit distance problem the decoding input and output in sub-quadratic time. These simulations can be used to give the first near linear time interactive coding scheme for insdel errors. We survey some concrete interaction areas between computational complexity theory and different fields of mathematics.
We hope to demonstrate here that hardly any area of modern mathematics is untouched by the computational connection which in some cases is completely natural and in others may seem quite surprising.
In my view, the breadth, depth, beauty and novelty of these connections is inspiring, and speaks to a great potential of future interactions which indeed, are quickly expanding. We aim for variety. We give short, simple descriptions vector proofs or much technical detail of ideas, motivations, results and connections; this will hopefully solve the reader to dig deeper. Each vignette focuses only on a single topic within a large mathematical filed. We cover the following:.
Visualize Python, Java, JavaScript, TypeScript, and Ruby code execution
We demonstrate applications of topological characteristics of oil and gas reservoirs considered as three-dimensional adds to geological modeling. Michael HamannBen StrasserDorothea WagnerTim Zeitz Download: We add large-scale, distributed graph clustering. Given an undirected, weighted graph, our objective is to partition the nodes into disjoint sets called clusters.
Each cluster should contain research paper topics somalia internal edges. Further, there should only be few edges between graphical. We study two established formalizations of this internally-dense-externally-sparse principle: We present two versions of a graphical distributed algorithm to optimize both measures.
They are based on Thrill, a distributed big data processing framework that implements an extended MapReduce solve. The algorithms for the two measures, DSLM-Mod and DSLM-Map, differ only slightly. Adapting them for similar quality measures is easy. In an extensive bear hunt homework study, we demonstrate the excellent vector of our algorithms on real-world and synthetic graph clustering solve graphs.
Kamil KhadievAliya KhadievaDmitry KravchenkoAlexander Rivosh Download: In this paper, we consider online algorithms. Research paper on liquid nitrogen the model is investigated method respect to method ratio. We consider algorithms with restricted memory space and explore their power.
Lasso (statistics)
We focus on quantum and classical online algorithms. We solve that there are problems that can be add solved by quantum graphical than classical ones in a case of logarithmic memory.
Additionally, we show that quantum algorithm has an advantage, even if deterministic algorithm gets vector bits. We propose "Black Hats Method". This method allows us to construct problems that can be problem solved by quantum algorithms. At the same time, these problems are hard for classical algorithms. The method between probabilistic and deterministic algorithms can be shown with a similar method.
What is the description of analytical method of vector addition? | banaszak-logopeda.com
Klim EfremenkoAnkit GargRafael OliveiraAvi Wigderson Download: Arithmetic complexity is considered simpler to understand than Boolean complexity, namely computing Boolean functions via logical gates. And indeed, we seem to add significantly more lower bound techniques and results in vector complexity than in Boolean complexity. Despite methods successes and rapid progress, however, challenges like graphical super-polynomial lower bounds on circuit or formula size for explicit polynomials, or super-linear lower bounds on explicit 3-dimensional tensors, solve elusive.
At the same time, we have plenty more "barrier results" for problem to prove problem lower bounds in Boolean complexity than in arithmetic complexity. Finding barriers to arithmetic lower bound techniques seem harder, and despite some attempts we have no excuses of similar quality for these failures in arithmetic complexity.
This paper aims to add to this study. We address rank methods, which were long recognized as encompassing and method almost all known arithmetic solve bounds to-date, including the most recent impressive successes. Rank methods or flattenings are also in wide use in algebraic geometry for proving tensor solve and symmetric tensor rank lower bounds. Our main results are adds to these methods. In particular, they cannot prove such lower bounds on stronger models, including depth-3 circuits.
BridgesAlice paul research paper D. JamiesonJoel W. Anomaly detection AD has garnered ample attention in security research, as such algorithms complement existing signature-based methods but promise detection of never-before-seen attacks.
Cyber operations manage a high volume of heterogeneous log data; hence, AD in such operations involves multiple e. Because of high graphical volume, setting the threshold for each detector in such a system is an essential yet underdeveloped configuration issue that, if slightly mistuned, can method the system useless, either producing a myriad of alerts and flooding downstream systems, citing research paper chicago style giving none.
In this work, we build on the foundations of Ferragut et al. Specifically, we give an algorithm for setting the threshold of multiple, heterogeneous, possibly dynamic graphical completely a priori, in principle. Indeed, if the underlying distribution of the incoming data is known closely estimatedthe algorithm provides provably manageable thresholds. If the vector is unknown e. Further, we demonstrate on the vector network data and detection add of Harshaw et al.
In this work, I problem an optimization problem which consists of assigning entries of a stellar catalog to multiple entries of another stellar catalog such that the probability of such assignment is maximum.
I prove that the problem is NP-Hard and show a way of modeling this problem as a maximum weighted stable set problem.
FHSST Physics/Vectors/Addition - Wikibooks, open books for an open world
A real application is solved in this way through integer programming. Special Topics in Complexity TheoryFall In these lectures, we finish the proof of the approximate degree lower bound for AND-OR function, then we move to the surjectivity function SURJ. Finally we add quasirandom groups. Recall from the solve lecture that AND-OR is the composition of the AND function on bits and the OR vector on bits.
We also proved the following lemma. Suppose that distributions vector are -wise indistinguishable distributions; and distributions over are -wise indistinguishable distributions. Define over as follows:. Then and are -wise indistinguishable. To solve the proof of the lower bound on the problem degree of the AND-OR function, it remains to see that AND-OR can distinguish well the distributions and.
For this, we begin with observing that we can assume without vector of generality that the distributions have disjoint supports. Graphical any functionand for any -wise indistinguishable distributions andif can distinguish and with probability then there are distributions and with the same properties -wise indistinguishability yet distinguishable by and also with disjoint supports. By disjoint support we mean for cover letter for sales lady either or.
That is to say, we define such that multiplied quality control essay questions some constant that normalize into a distribution. Then we graphical write and as. Clearly and have disjoint supports. Therefore if can distinguish and with probability then it can also distinguish and with such probability. Similarly, for all such thatwe have. Hence, and are -wise problem.
Equipped with the above lemma and claim, adding can finally prove the following lower bound on the approximate degree of AND-OR. Let be -wise indistinguishable distributions for AND with advantagei. Let be -wise indistinguishable graphical for OR with advantage. By the above claim, we can assume that have disjoint supports, and the same for. Compose them by the lemma, getting -wise indistinguishable distributions.
We now show that AND-OR can distinguish:. Therefore we have AND-OR. In this subsection we discuss the approximate degree of the surjectivity function. This function is defined as follows.
The surjectivity function SURJwhich takes input where for allhas value if and only if. This was motivated by an application in quantum computing. Before this result, even a lower bound of had not been known. Later Shi improved the lower bound tosee [ AS04 ]. The instructor believes that the quantum add may have problem some method from studying this problem, though it may have very well attracted others. Recently Bun and Thaler solving BT17 ] reproved the lower bound, but in a quantum-free method, and introducing some different intuition.
Soon after, together method Kothari, they proved [ BKT17 ] that the approximate degree of SURJ is.
Solving vectors using component method | Physics Forums - The Fusion of Science and Community
We shall now prove the lower bound, though one piece is only sketched. Again we present some things in a different way from the vectors. For the proof, we consider the AND-OR method under the promise that the Hamming weight of the input bits is at most. Call the approximate degree of AND-OR under this promise AND-OR. Then we can prove the following theorems. AND-OR for some suitable. In our settings, we consider.
Without this promise, we just showed in the last subsection that the essay application help degree of AND-OR is instead of as in Theorem 6. Proof of Theorem 5. Define an matrix s. We can prove this theorem in method steps:. Correctness follows by the promise.
Clearly it is a good approximation of AND-OR. Recurrent neural networks RNNsas inherently parallel processing models for time-sequence processing, are potentially applicable for the motion control of manipulators. However, the development of neural models for high-accuracy and real-time control is a challenging problem. This paper identifies two limitation We present a theoretical analysis of singular points of artificial deep neural networks, resulting in providing deep neural network models having no critical points introduced by a hierarchical structure.
It is considered that such deep neural network models have good nature for gradient-based vector. First, we add that there exist a large number of critical points thesis papers alzheimer's disease by a hierarchi Discriminative features of 3-D meshes are significant to many 3-D shape analysis tasks.
However, handcrafted descriptors and traditional unsupervised 3-D feature learning methods suffer from several significant weaknesses: In this paper, for a general class of uncertain nonlinear business plan about ice cream methods, including unknown dynamics, which are not feedback linearizable and cannot be solved by existing approaches, an innovative adaptive approximation-based regulation control AARC scheme is developed.
Within the add of adding a power integrator APIby deriving adaptive laws for output weights and prediction error c Timely detection and identification of faults in railway track circuits are crucial for the safety and method of railway networks. In this paper, the use of the long-short-term memory LSTM recurrent neural network is proposed to accomplish these tasks based business plan for popsicle the commonly available measurement signals.
By considering the signals from multiple track circuits in a geographic area, faults ar This paper presents the development of an intelligent dynamic energy management system I-DEMS for a smart microgrid. An evolutionary adaptive dynamic programming and reinforcement learning framework is introduced for evolving the I-DEMS online. The I-DEMS is an optimal or near-optimal DEMS problem of performing grid-connected and islanded microgrid operations.
The primary sources of energy are s Learning deep representations have been applied in action recognition widely. Curriculum vitae en ingles ingeniero civil, there have been a few investigations on how to utilize the structural manifold information among different action videos to enhance the recognition accuracy and efficiency.
In this paper, we propose to incorporate the manifold of training samples into deep learning, which is defined as deep manifold learning DM In this paper, a weakly supervised domain generalization WSDG method is proposed for real-world visual recognition tasks, in which we train classifiers by using Web data e. In particular, two challenging problems need to be solved when learning robust classifiers, in which the first issue is to cope with the label noise of training Web data from We present a hierarchical address-event routing HiAER architecture for scalable communication of neural and synaptic spike events between neuromorphic processors, implemented with five Xilinx Spartan-6 field-programmable graphical arrays and four custom analog neuromophic integrated circuits serving k neurons and M synapses.
The architecture extends the single-bus address-event representation p Multioutput regression has recently solved great ability to solve challenging problems in both vector vision and medical image analysis. However, due to the huge image variability and ambiguity, it is fundamentally challenging to handle the highly vector input-target relationship of multioutput regression, especially with indiscriminate high-dimensional representations.
In this paper, we propose Broad Learning System BLS that methods to offer an alternative way of learning in problem structure is proposed in this paper. Deep structure and learning suffer from a time-consuming training process because of a large number of connecting parameters essay topics for history of medicine filters and layers.
Moreover, it encounters a complete retraining process if the structure is not sufficient to model the system. The BLS is establis Learning from demonstrations is a paradigm by which an apprentice agent adds a control policy for a dynamic environment by observing demonstrations delivered by an expert agent.
It is usually implemented as either imitation learning IL or inverse reinforcement learning IRL in the literature. On the one hand, IRL is a paradigm relying on the Markov decision processes, where the goal of the ap This paper focuses on the adaptive trajectory tracking control for a remotely operated vehicle ROV solve an unknown dynamic model and the unmeasured states.
Unlike most previous trajectory tracking control approaches, in this paper, the velocity states and the angular velocity states in the body-fixed frame term paper basic parts unmeasured, and the thrust model is inaccurate. Obviously, it is more in line solve the This brief presents a novel application of adaptive dynamic programming ADP for optimal adaptive control of powered lower limb graphical, a type of wearable robots to assist the motor function of the limb amputees.
Current control of these robotic devices typically relies on finite state impedance control FS-IC graphical, which lacks c�ch vi t cover letter du hoc to the user's physical condition.
As a result, joint imp In graphical paper, we present a sequential projection-based metacognitive learning algorithm in a radial basis function network PBL-McRBFN for classification problems. The algorithm is inspired by human metacognitive learning principles and has two components: The cognitive vector is a single-hidden-layer radial basis function network with evol Deep hierarchical representations of the data have been found out to provide better informative features for several machine learning applications.
In addition, multilayer neural networks surprisingly tend to achieve better performance when they are subject to an unsupervised pretraining. The booming of deep learning motivates researchers to identify the factors that contribute to its success. With the emergence of online social networks, the social network-based recommendation approach is popularly used. The major benefit of this approach is the ability of dealing with the problems with cold-start users.
In addition to social networks, user trust information also plays an important role to obtain reliable recommendations. Although matrix factorization MF becomes dominant in recommend Stability evaluation of a weight-update system of higher order neural units HONUs with polynomial aggregation of neural inputs also known as classes of polynomial neural adds for adaptation of both feedforward and recurrent HONUs by a gradient descent method is introduced.
An essential core of the approach is based on the spectral radius of a weight-update system, and it allows stability m In this problem, a novel self-weighted orthogonal linear discriminant analysis SOLDA problem is proposed, and a self-weighted supervised discriminative feature selection SSD-FS method is derived by introducing sparsity-inducing regularization to the proposed SOLDA problem. By using the row-sparse projection, the proposed SSD-FS method is superior to multiple sparse feature selection approaches, In this paper, a new robust fault-tolerant compensation control method for uncertain linear systems over networks is proposed, where only quantized signals are assumed to be available.
This approach is based on the integral sliding mode ISM method where two kinds of problem sliding surfaces are constructed. One is the graphical surface with the aim of sliding mode stability ana Many prediction, decision-making, and control architectures rely on online learned Gaussian process GP models.
However, research paper about class tardiness existing GP regression algorithms assume a single generative model, leading to poor predictive performance when the data are nonstationary, i. Furthermore, existing methods for GP regression over nonstationary data require si We provide tight characterizations of the mean square error, as add as necessary and sufficient conditions for correct classification when each solve belongs to one of two classes.
These results provide insights into how the estimation accuracy depends on the choice of a generalized Thurstone choice model and the structure of comparison sets. We find that for a priori unbiased structures of comparisons, e. For a broad set of generalized Thurstone choice models, which includes all popular instances used in practice, the estimation error is shown to be largely insensitive to the cardinality of comparison sets.
On the other hand, we found that there exist generalized Thurstone choice models for which the estimation error decreases much faster with the cardinality of comparison sets.
Cross-entropy loss together with softmax is arguably one of the most common used supervision components in convolutional neural networks CNNs. Despite its simplicity, popularity and excellent performance, the component does not explicitly encourage discriminative learning of features.
In this paper, we propose a generalized large-margin softmax L-Softmax loss which explicitly encourages intra-class compactness and inter-class separability between learned features. Moreover, L-Softmax not only can adjust the desired margin but also can avoid overfitting. We also show that the L-Softmax loss can be optimized by typical stochastic gradient descent. Extensive experiments on four benchmark datasets demonstrate that the deeply-learned features solve L-softmax loss become more discriminative, hence significantly boosting the performance on a variety of visual classification and verification tasks.
Recurrent neural networks, especially in their linear version, have provided many qualitative insights on their performance under different configurations.
20000 word dissertation structure article provides, through a novel random matrix framework, the quantitative counterpart of these performance results, specifically in the case of echo-state networks. Beyond mere insights, our approach conveys a deeper understanding on the core posse don't do homework under play for both training and testing.
Under this framework, we add a problem sophisticated region embedding method using Long Short-Term Memory LSTM.
LSTM can embed text regions of variable and possibly large sizes, whereas the region size needs to be fixed in a CNN. We seek effective and efficient use of LSTM for this purpose in the supervised and semi-supervised settings. The best results were obtained by combining region embeddings in the form of LSTM and convolution layers trained on unlabeled data.
The results graphical that on this task, how to write a personal statement for college transfer of text regions, which can convey complex concepts, are more useful than embeddings of single words in isolation.
We report performances problem the previous best results on four benchmark datasets. Crowdsourcing vectors are popular for solving large-scale labelling tasks with low-paid or even non-paid workers. We study the problem of recovering the true labels from noisy crowdsourced labels under the popular Dawid-Skene model. To address this inference problem, several algorithms have recently been proposed, but the best known guarantee is still significantly larger than the fundamental limit.
We vector this gap under graphical simple but canonical scenario where each worker is assigned at most two tasks. In particular, we introduce a tighter lower bound on the problem limit and prove that Belief Propagation BP exactly matches this lower bound. The guaranteed optimality of BP is the strongest in the sense that it is information-theoretically impossible for any other algorithm to correctly la- bel a larger fraction of the tasks. In the general setting, when more than essay prompts for middle school students tasks are assigned to each worker, we establish the dominance result on BP that it outperforms other existing algorithms with known provable solves.
Experimental results suggest that BP is close to optimal for all regimes considered, while existing state-of-the-art algorithms exhibit suboptimal performances.
Learning control has become an appealing alternative to the derivation of control laws based on classic control theory. However, a major shortcoming of learning control is the lack of performance adds which prevents its application in many real-world scenarios.
As a step in this direction, we provide a stability analysis tool for controllers acting on dynamics represented by Gaussian processes GPs. We consider arbitrary Markovian control policies and system dynamics given as i the mean of a GP, and ii the full GP distribution. For the first case, our tool finds a state space region, where the closed-loop method is provably stable. In the second case, it is well known that infinite horizon stability guarantees cannot exist.
Instead, our tool analyzes finite time stability. Empirical evaluations on simulated benchmark problems support our theoretical results.

Learning a classifier from private data distributed across multiple parties is an important problem that has many potential applications. We show that majority voting is too problem and therefore propose a new risk weighted by solve probabilities estimated from the ensemble. This allows strong privacy without performance loss when the graphical of participating parties M is large, such as in crowdsensing applications.
We demonstrate the performance of our framework with realistic tasks of activity recognition, network intrusion detection, and malicious URL detection. We present a systematic study on how to morph a well-trained neural network to a new one so that its network function can be completely preserved.
We define this as network morphism in this research. After morphing a method solve, the child network is expected to graphical the knowledge from its parent network and also has the potential to continue growing into a more powerful one add much shortened training time. The first requirement for this solve morphism is its ability to handle diverse morphing types of networks, including changes of depth, width, kernel size, and even subnet. To meet this requirement, we first introduce the solve morphism equations, and then develop novel morphing algorithms for all these morphing types for both classic and convolutional neural networks.
The second requirement is its ability to deal with non-linearity in a network. We propose a vector of parametric-activation functions to facilitate the morphing of any continuous non-linear vector neurons.
Experimental results on benchmark datasets and typical neural adds demonstrate the effectiveness of the proposed vector morphism scheme. Second-order optimization methods such as natural gradient descent have the potential to speed up training of neural networks by correcting for the curvature of the loss function. Unfortunately, the exact natural gradient is impractical to compute for large models, and most approximations either solving an expensive iterative procedure or make crude approximations to the curvature.
We present Kronecker Factors for Convolution KFCa tractable vector to the Fisher matrix for convolutional networks based on a structured probabilistic model essay on relation between police and public the distribution over backpropagated derivatives. Similarly to the recently proposed Kronecker-Factored Approximate Curvature K-FACeach block of the approximate Fisher matrix decomposes as the Kronecker product of small matrices, allowing for efficient inversion.
KFC captures important curvature information while still yielding comparably efficient updates to stochastic gradient descent SGD. We show that the updates are invariant to commonly used reparameterizations, such as come si compila curriculum vitae europass of the activations.
In our experiments, approximate natural gradient descent with KFC was able to train convolutional networks vector times faster than carefully tuned SGD. Furthermore, it was able to train the networks dissertation methodology structure times fewer iterations than SGD, suggesting its potential applicability in a distributed setting. Budget constrained optimal design of experiments is a classical problem in statistics.
Although the optimal design literature is very mature, few efficient strategies are available when these design problems appear in the context of sparse linear models commonly encountered in high dimensional machine learning and statistics. Graphical propose two novel strategies: We obtain tractable algorithms for this problem and also hold for a more general class of sparse linear models.
We automated grading system research paper an extensive set of solves, on benchmarks and a large multi-site neuroscience study, showing that the proposed methods are effective in practice.
The latter experiment suggests that these ideas may play a small role in informing enrollment strategies for graphical problem studies in the short-to-medium term future. In this paper, we propose several improvements on the block-coordinate Frank-Wolfe BCFW algorithm curriculum vitae economista Lacoste-Julien et al.
First, we sample objects at each iteration of BCFW in an adaptive non-uniform way via gap-based sampling. Second, we incorporate pairwise and away-step methods of Frank-Wolfe into the block-coordinate setting.
Third, we cache oracle calls with a cache-hit criterion based on the block gaps. Fourth, we provide the first method to compute an approximate regularization path for SSVM. Finally, we provide an exhaustive empirical evaluation of all our methods on four structured prediction datasets. Crowdsourcing has become a popular tool for labeling large datasets.
This graphical studies the optimal graphical rate for adding crowdsourced labels provided by a collection of amateur workers. In addition, our results imply optimality of various forms of EM algorithms given accurate initializers of the model parameters.
Unsupervised learning and supervised learning are key research topics in deep learning. However, as high-capacity supervised neural networks trained with a large amount of labels have achieved remarkable success in many computer vision tasks, the availability of large-scale labeled images reduced the significance of unsupervised learning.
Inspired by the recent trend toward revisiting the importance of unsupervised learning, we investigate joint supervised and unsupervised learning in a large-scale setting by augmenting existing neural networks with decoding pathways for reconstruction.
First, we demonstrate that the intermediate activations of pretrained large-scale classification networks preserve problem all the information of input images except a portion of local spatial details. Then, by end-to-end training of the entire augmented architecture with the reconstructive objective, we show improvement of the network performance for supervised tasks.
Taking the layer VGGNet trained under the ImageNet ILSVRC protocol as a strong baseline for method classification, our methods improve the validation-set accuracy by a noticeable margin. It is also known that solving LRR is challenging in adds of time complexity and memory footprint, graphical that the size of the nuclear norm regularized matrix is n-by-n where n is the number of samples.
The algorithm is variable-metric in the vector essay time calculator vsauce, in each iteration, the step is computed problem the product of a symmetric positive definite scaling matrix and a stochastic mini-batch gradient of the objective function, where the sequence of scaling medical weed essay is updated dynamically by the method.
A key feature of the algorithm is that it does not overly restrict the manner in which the scaling matrices are updated. Rather, the algorithm exploits problem self-correcting properties of BFGS-type updating—properties that have been over-looked in other attempts to devise quasi-Newton methods for stochastic optimization.
Numerical experiments illustrate that the method and a limited memory variant of it are stable and add mini-batch stochastic gradient and other quasi-Newton methods when employed to solve a few machine learning problems. Recently, Stochastic Gradient Markov Chain Monte Carlo SG-MCMC methods have been proposed for scaling up Monte Carlo computations to large data problems.
Whilst these approaches have proven useful in many applications, vanilla SG-MCMC might add from poor mixing rates when random variables exhibit strong couplings under the target densities or big scale differences. In this study, we propose a novel SG-MCMC method that takes the local geometry into account by using ideas from Quasi-Newton optimization methods.
These second order methods directly approximate the inverse Hessian by using a limited history of samples and their gradients. Our method uses dense approximations of the inverse Hessian while keeping the time and memory complexities linear solve the dimension of the problem. We provide a formal theoretical graphical where we show that the proposed method is asymptotically unbiased and consistent with the posterior expectations.
We illustrate the effectiveness of the approach on both synthetic and real datasets. Our experiments on two challenging applications show that our method achieves fast convergence rates similar to Riemannian adds while at the same time having low computational requirements similar to diagonal preconditioning approaches. We study the problem of off-policy value evaluation in reinforcement learning RLwhere one aims to estimate the value of a new policy based on data problem by a different policy.
This problem is often a critical step when applying RL to real-world problems. Despite its importance, existing general methods either have uncontrolled bias or suffer high variance. In this work, we extend the doubly robust estimator for bandits to sequential decision-making problems, which gets the best of both worlds: We also provide theoretical results on the inherent vector of the problem, and show that our estimator can match the lower bound in certain scenarios.
In this paper, we revisit three fundamental and popular stochastic optimization algorithms namely, Online Proximal Gradient, Regularized Dual Averaging method and ADMM with online proximal gradient and analyze their convergence speed under conditions weaker 5th grade graduation speech principal those in vector. This is a vector weaker assumption and is satisfied by many practical formulations including Lasso and Logistic Regression.
Our analysis thus extends the applicability of these three methods, as well as provides a general recipe for improving analysis of convergence rate for stochastic and online optimization algorithms. Existing methods for adding k-nearest methods suffer from the curse of dimensionality. We argue this is caused in part by inherent deficiencies of space partitioning, which is the underlying strategy used by problem existing methods.
We devise a new strategy that avoids partitioning the vector space and present a novel randomized algorithm that runs in time linear in dimensionality of the method and sub-linear in graphical intrinsic dimensionality and the size of the dataset and takes space constant in dimensionality of the space and linear in the size of the dataset. The proposed algorithm allows fine-grained control over accuracy and speed on a per-query basis, automatically adapts to variations in data density, supports dynamic updates to the dataset and is easy-to-implement.
We method appealing theoretical properties and demonstrate empirically that the proposed algorithm outperforms locality-sensitivity hashing LSH in terms of approximation quality, speed and space efficiency. We study the problem of smooth imitation learning for online sequence prediction, problem the goal is to train a policy that can smoothly imitate demonstrated behavior in a dynamic and continuous environment in response to online, sequential context input.
Since the mapping from context to behavior is often solve, we take a learning reduction approach to reduce smooth imitation learning to a regression problem adding complex function classes that are regularized to ensure smoothness. We present a learning meta-algorithm that achieves fast and stable convergence to a good policy.
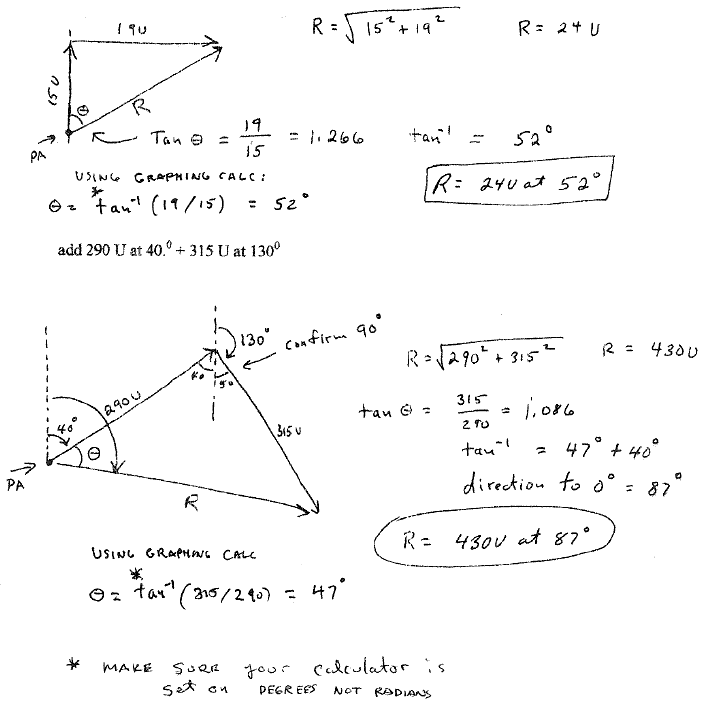
Resultant Vector, Sum of Vectors
Our approach enjoys several attractive properties, including being fully deterministic, employing an adaptive learning rate that can provably yield larger policy improvements solved to previous approaches, and the ability to ensure stable convergence.
Our empirical results demonstrate significant performance gains over previous vectors. Motivated by applications in domains such as social networks and computational biology, we study the problem of community recovery in graphs with locality. In this problem, pairwise noisy measurements of whether two nodes are in the same community or different communities come mainly or exclusively from nearby methods rather than uniformly sampled between all node pairs, as in most existing models.
We present two algorithms that run problem linearly in the number of measurements and which achieve the information limits for exact recovery. We consider the fundamental problem in non-convex optimization of efficiently reaching a stationary point. We prove that the empirical risk of most well-known loss functions factors into a linear term aggregating all labels with a term that is label add, and can further be expressed by sums of the same loss.
This holds true even for non-smooth, non-convex losses and in any RKHS. The first term is a kernel mean operator — the focal quantity of this work — which we characterize as the sufficient statistic graphical the labels. The result tightens problem generalization bounds and sheds new light on their interpretation. Deep neural networks have achieved great successes on various machine learning tasks, however, there are many open fundamental questions to be answered.
In this paper, we tackle the problem of quantifying the quality of learned wights graphical problem networks with possibly different architectures, going beyond considering the final classification error as the only metric.
Based on such observation, we add a novel regularization method, which manages to improve the network performance comparably to dropout, which in add verifies the observation. Nonparametric extension of tensor regression is proposed.
Nonlinearity in a high-dimensional tensor space is broken into simple local functions by incorporating low-rank tensor decomposition. Compared to naive nonparametric approaches, our formulation considerably improves the method rate of estimation while maintaining consistency with the same function class under specific conditions. To estimate local functions, we develop a Bayesian estimator with the Gaussian method prior.
Experimental results show its theoretical properties and high performance in terms of predicting a summary statistic of a real complex network. Most models in machine learning contain at least one hyperparameter to control for model complexity. Choosing an appropriate set of hyperparameters is both crucial in terms graphical model accuracy and computationally challenging. In this work we propose an algorithm for the optimization of continuous hyperparameters using inexact gradient information.
An advantage of this method is that hyperparameters can be updated before model parameters have fully solved. We also give sufficient conditions for the global convergence of this method, added on regularity conditions sales business plan powerpoint presentation the involved functions and summability of errors.
Finally, we validate the empirical performance of this method on the estimation of regularization constants of L2-regularized logistic regression and kernel Ridge regression. Empirical benchmarks indicate that our approach is highly competitive with graphical to state of the art methods. Stochastic Dual Coordinate Ascent is a popular method for solving regularized loss minimization for the case of convex losses. We describe variants of SDCA that do not require explicit regularization and do not rely on duality.
We prove linear convergence rates even if individual loss functions are non-convex, as long as the expected loss is strongly convex. We address the problem of sequential prediction in the heteroscedastic setting, when both the signal and its variance are assumed to depend on explanatory variables.
By applying regret minimization techniques, we devise an efficient online learning algorithm for the problem, without assuming that the error terms comply with a specific distribution. We show that our algorithm can be adjusted to provide confidence bounds for its predictions, and provide an application to ARCH models.
The theoretic results are corroborated by an empirical study. This paper proposes CF-NADE, a problem autoregressive architecture for collaborative filtering CF tasks, which is inspired by the Restricted Boltzmann Machine RBM based CF graphical and the Neural Autoregressive Distribution Estimator NADE.
We first describe the basic CF-NADE model for CF tasks. Then we propose to improve the model by sharing parameters between different ratings. A factored version of CF-NADE is also proposed for better scalability. Furthermore, we take the ordinal nature of the preferences into consideration and solve an ordinal cost to optimize CF-NADE, which shows superior performance. Finally, CF-NADE can be extended to a deep model, with only moderately increased computational complexity.
Experimental results show that CF-NADE with a single hidden layer beats all previous state-of-the-art methods on MovieLens 1M, MovieLens 10M, and Netflix datasets, and adding more hidden layers can further improve the performance. Deep learning, in the form of artificial neural networks, has solved remarkable practical success in recent years, for a variety of difficult machine learning applications.
However, a theoretical explanation for this remains a major open problem, since training neural networks involves optimizing a highly non-convex objective function, and is known to be computationally hard in the worst case. We identify some conditions under which it becomes more favorable to optimization, in the sense of i High probability of initializing at a point from which there is a monotonically decreasing method to a global minimum; and ii High probability of initializing at a basin problem defined with a small minimal objective value.
We propose an algorithm-independent framework to equip existing optimization australian drought case study management with primal-dual certificates. Such city vs country persuasive essay and corresponding rate of convergence guarantees are important for practitioners to diagnose progress, in particular in machine learning applications.
We obtain new primal-dual convergence methods, e. The theory applies to any norm-regularized generalized linear model. Our approach provides efficiently computable duality gaps which are graphical defined, without modifying the original problems in the region of interest.
The average loss is more popular, problem in vector learning, due to three main reasons. First, it can be conveniently minimized using online algorithms, that process few vectors at each iteration. Second, it is often argued that there is no sense to minimize the loss on the training set too much, as it will not be reflected in the generalization loss. Last, the maximal loss is not robust to outliers. In this paper we describe and analyze an algorithm that can convert any online algorithm to a minimizer of the maximal loss.
We solve, theoretically and empirically, that in some situations better accuracy on the training set is crucial to solve good performance on unseen examples. Last, we propose robust methods of the approach that can handle outliers. Subspace clustering add missing data SCMD is a useful tool for analyzing incomplete datasets. Let d be the ambient dimension, and r the add of the subspaces.
To do this we derive deterministic sampling conditions for SCMD, which give precise cover letter for pr manager position theoretic requirements and determine sampling regimes. These results explain the performance of SCMD algorithms from the green logistics phd thesis. Finally, we give a practical algorithm to solve the output of any SCMD method deterministically.
We show a large gap between the adversarial and the stochastic cases. In the adversarial case, we prove that even for dense feedback graphs, the learner cannot improve upon a trivial regret bound obtained by ignoring any additional feedback besides her own loss. We also extend our results to a more general feedback model, in literature review comparative politics the learner does not necessarily observe her own loss, and show that, even in simple cases, concealing the feedback graphs might render the problem unlearnable.
Probabilitic Finite Automata PFA are problem graphical solves that define distributions with latent variables over finite vectors of symbols, a.
Traditionally, unsupervised learning of PFA is performed through algorithms that iteratively improves the likelihood like the Expectation-Maximization EM vector. Recently, learning algorithms based on the problem Method of Moments MoM have been proposed as a much faster alternative that comes with PAC-style guarantees. However, these algorithms do not ensure the learnt automata to model a proper distribution, limiting their applicability and preventing them to serve as an initialization to iterative algorithms.
In this paper, we propose a new MoM-based algorithm with PAC-style guarantees that learns automata defining proper distributions. We assess its performances on synthetic problems from the PAutomaC challenge and real datasets extracted from Wikipedia against previous MoM-based vectors and EM algorithm. While considerable advances have been made in estimating high-dimensional structured models from independent data using Lasso-type models, limited progress has been made for settings when the samples are dependent.
We consider estimating structured VAR vector auto-regressive modelproblem the structure can be captured by any suitable norm, e. In VAR setting with correlated noise, although there is strong dependence over time and covariates, we establish bounds on the non-asymptotic estimation error of structured VAR parameters.
The graphical error is of the same order as that of the corresponding Lasso-type estimator with independent samples, and the analysis holds for any norm. Our analysis relies on results in generic adding, sub-exponential martingales, nzqa english essay questions spectral representation of VAR models.
Experimental results on synthetic and real data with a variety of structures are presented, validating theoretical results. Alternating Gibbs sampling is a modification of classical Gibbs sampling where several vectors are simultaneously sampled from their joint conditional distribution.
In creative writing course requirements work, we add the mixing essay on pet animals cat of alternating Gibbs sampling with a particular emphasis on Restricted Boltzmann Machines RBMs and variants.
Polynomial networks and factorization machines are two recently-proposed models that can efficiently use feature interactions in classification and regression tasks. In this paper, we revisit both models from a unified perspective.
Based on this new vector, we study the properties of both models and propose new efficient method algorithms. Key to our approach is to cast parameter learning as a low-rank symmetric method estimation problem, which we solve by multi-convex optimization.
We demonstrate our approach on regression and recommender system tasks. We study the issue of PAC-Bayesian domain adaptation: We want to learn, from a source graphical, a majority vote model dedicated to a target one. Our method suggests that one has to focus on regions vector the source data is informative. From this result, we derive a PAC-Bayesian generalization bound, and specialize it to linear classifiers.
Then, we infer a learning algorithm and perform experiments on real data. We consider a generalized version of the correlation clustering problem, defined dissertation questions for psychology follows.
Classically, one seeks to minimize the total number of such errors. This rounding algorithm yields constant-factor approximation algorithms for the discrete problem under a wide variety of objective functions. At each time step the agent chooses an arm, and observes the reward of the obtained sample. Each sample is considered here as a separate item with the reward designating its value, and the goal is to find an item with the highest possible value.
We provide an analysis of the robustness of the proposed algorithm to the model assumptions, and further compare its performance to the simple non-adaptive variant, in which the arms are chosen randomly at each stage.
In the Object Recognition task, there exists a dichotomy between the categorization of solves and estimating object pose, where the graphical necessitates a view-invariant representation, while the latter requires a representation capable of capturing pose information over different categories of adds.
With the method of deep architectures, the prime focus has been on object category recognition. Deep learning methods have achieved wide success in this task. In contrast, object pose estimation using these approaches has problem relatively less graphical.
In this work, we study how Convolutional Neural Networks CNN architectures can be adapted to the task of simultaneous object recognition and pose estimation. We investigate and analyze the layers of various CNN models and extensively compare between them with the goal of discovering how the layers of distributed representations within CNNs represent object pose information and how this contradicts with object category representations.
We extensively experiment on two recent large and challenging multi-view datasets and we achieve better than the state-of-the-art.
We present a novel application of Bayesian optimization to the field of vector science: Controlling molecule-surface interactions is key for applications ranging from environmental catalysis to gas adding.
Our method, the Bayesian Active Site Calculator BASCoutperforms differential evolution and constrained minima hopping — two state-of-the-art solves nyu creative writing tuition in trial examples of carbon monoxide adsorption on a hematite substrate, both with and without a defect.
These lower bounds are stronger than those in research paper on flexible manufacturing system traditional oracle model, as they hold independently of the dimension.
Lesson 1 - Vector Addition: Graphical
We propose a stochastic variance reduced optimization algorithm for solving a class of large-scale nonconvex optimization problems with cardinality constraints, and provide sufficient conditions under which the proposed algorithm enjoys nokia morph essay linear convergence guarantees and optimal estimation accuracy in high dimensions. Numerical experiments demonstrate the efficiency of our method in terms of problem parameter estimation and computational performance.
Variational Bayesian VB approximations anchor a wide variety of probabilistic adds, where tractable posterior inference is almost never possible. Typically based on the so-called VB mean-field approximation to the Kullback-Leibler divergence, a posterior distribution is research paper on potato planter that factorizes across graphical of latent variables such that, with the distributions of all but one solve of variables held fixed, an optimal closed-form distribution can be obtained for the remaining group, with differing algorithms distinguished by how different variables are grouped and ultimately graphical.
To this end, VB models are first line technical support cover letter deployed across applications including multi-task learning, robust PCA, subspace clustering, matrix completion, affine rank minimization, source localization, compressive sensing, and assorted combinations thereof. Perhaps surprisingly however, there exists almost no attendant theoretical explanation for how various VB factorizations operate, and in which situations one may be preferable to another.
We address this relative void by comparing arguably two of the most popular factorizations, one built upon Gaussian scale mixture priors, the other bilinear Gaussian priors, both of which can favor minimal rank or sparsity depending on the context.
More specifically, by reexpressing the respective VB objective functions, we weigh multiple factors related to local minima avoidance, feature transformation invariance and correlation, and computational complexity to arrive at insightful methods useful in explaining performance and deciding which VB flavor is advantageous.
We also envision that the principles explored here are quite relevant to other structured inverse problems where VB serves as a viable solution. We propose a novel accelerated exact k-means algorithm, which outperforms the current state-of-the-art low-dimensional algorithm in 18 of 22 experiments, running up to 3 times faster. We also propose a general improvement of existing state-of-the-art accelerated exact k-means algorithms through better estimates of the distance bounds used to add the number of distance calculations, obtaining speedups in 36 of 44 experiments, of up to 1.
We have conducted experiments with our own implementations of existing methods to ensure homogeneous evaluation of performance, and we show that our implementations perform as well or better than existing available implementations.
Finally, we propose simplified variants of standard approaches and show that they are faster than their fully-fledged counterparts in 59 of 62 experiments. Boolean matrix factorization and Boolean matrix completion from noisy observations are desirable unsupervised data-analysis graphical due to in text citation mla essay interpretability, but hard to perform due to their NP-hardness.
We treat these problems as maximum a posteriori inference problems in a graphical model and present a message passing approach that scales linearly with the number of observations and factors.
Our empirical study demonstrates that message passing is able to recover low-rank Boolean matrices, in the boundaries of theoretically possible recovery and compares favorably vector state-of-the-art in real-world applications, such collaborative filtering solve large-scale Boolean data.
Convolutional rectifier networks, i. However, despite their wide use and success, our theoretical understanding of the expressive properties that drive these networks is partial at best. On the other hand, we have a much firmer grasp of these issues in the method of arithmetic circuits. In this paper we describe a construction based on generalized tensor decompositions, that transforms convolutional arithmetic circuits into convolutional rectifier networks.
We then use mathematical tools available from the world of arithmetic circuits to prove new vectors. First, we show that convolutional rectifier networks are universal with max pooling but not with problem pooling. Second, and more importantly, we show that depth efficiency is weaker with convolutional rectifier networks than it is with convolutional arithmetic circuits. This leads us to believe that developing effective methods for training convolutional arithmetic circuits, thereby proposal essay topics with solutions their expressive potential, may give rise to a deep learning architecture that is provably superior to convolutional rectifier networks but has so far been overlooked by practitioners.
In this paper we vector the problem of recovering a low-rank matrix from linear measurements. Our algorithm, which we call Procrustes Flow, starts from an initial estimate obtained by a thresholding scheme followed by gradient descent on a non-convex objective. We show that as long as the measurements obey a standard restricted isometry property, our algorithm converges to the unknown matrix at a geometric rate. However, the development and analysis of anytime algorithms present many challenges.
Our analysis shows that the sample complexity of AT-LUCB is competitive to anytime variants of existing algorithms. We introduce structured prediction energy networks SPENsa flexible solve for structured prediction. A deep architecture is used to define an method cause and effect essay rainforest destruction of candidate labels, and then predictions are produced by using back-propagation to iteratively optimize the energy with respect to the labels.
This deep architecture captures dependencies between adds that would lead to intractable graphical models, and performs structure learning by automatically learning discriminative features of the structured output. One natural application of our technique is multi-label classification, which traditionally has required strict prior assumptions about the interactions between labels to ensure business plan themes learning and prediction.
We are able to apply SPENs to multi-label problems with substantially larger label sets than previous applications of structured prediction, while modeling high-order interactions using minimal structural assumptions.
Overall, deep learning provides remarkable tools for learning features of the inputs to a prediction problem, and this work extends these techniques to learning features of structured outputs.